If you’re looking to hide files on your PC hard drive, you may have read about ways to encrypt folders or change the attributes on a file so that they cannot be accessed by prying eyes. However, a lot of times hiding files or folders in that way requires that you install some sort of software on your computer, which could then be spotted by someone else.
I’ve actually written quite a few articles on how you can hide files and folders in Windows XP and Vista before, but here I’m going to show you a new way to hide files that is very counter-intuitive and therefore pretty safe! Using a simple trick in Windows, you can actually hide a file inside of the JPG picture file!
You can actually hide any type of file inside of an image file, including txt, exe, mp3, avi, or whatever else. Not only that, you can actually store many files inside of single JPG file, not just one! This can come in very handy if you need to hide files and don’t want to bother with encryption and all that other technical stuff.
Hide File in Picture
In order to accomplish this task, you will need to have either WinZip or WinRAR installed on your computer. You can download either of these two off the Internet and use them without having to pay anything. Here are the steps for creating your hidden stash:
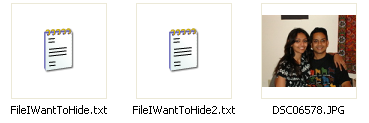
•Create a folder on your hard drive, i.e. C:\Test and put in all of the files that you want to hide into that folder. Also, place the image that you will be using to hide the files in.
I’ve actually written quite a few articles on how you can hide files and folders in Windows XP and Vista before, but here I’m going to show you a new way to hide files that is very counter-intuitive and therefore pretty safe! Using a simple trick in Windows, you can actually hide a file inside of the JPG picture file!
You can actually hide any type of file inside of an image file, including txt, exe, mp3, avi, or whatever else. Not only that, you can actually store many files inside of single JPG file, not just one! This can come in very handy if you need to hide files and don’t want to bother with encryption and all that other technical stuff.
Hide File in Picture
In order to accomplish this task, you will need to have either WinZip or WinRAR installed on your computer. You can download either of these two off the Internet and use them without having to pay anything. Here are the steps for creating your hidden stash:
•Create a folder on your hard drive, i.e. C:\Test and put in all of the files that you want to hide into that folder. Also, place the image that you will be using to hide the files in.